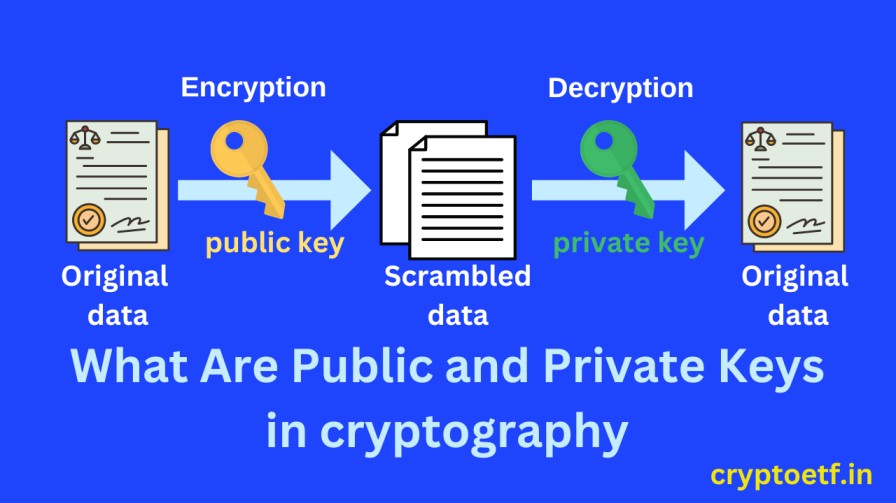
Cryptography is an essential tool for keeping information secure in the digital age. One of the most important concepts in cryptography is the use of public and private keys. These keys are used to encrypt and decrypt messages and data, ensuring that only authorized parties can access sensitive information.
Here, we will explore what public and private keys are, how they work, and why they are so important for cybersecurity.
What is a cryptographic key?
A cryptographic key is a piece of information used in cryptography to encrypt and decrypt data. It is a string of bits or characters that is used to transform plain text into cipher text or vice versa.
In symmetric key cryptography, the same key is used for both encryption and decryption. This key must be kept secret from anyone who is not authorized to access the encrypted data.
In public key cryptography, two different keys are used: a public key for encrypting data and a private key for decrypting it. The public key can be freely distributed, while the private key must be kept secret.
The strength of a cryptographic system depends on the secrecy and complexity of its keys. A weak key can make it easy for an attacker to break the encryption and access the sensitive information. Therefore, generating and managing secure cryptographic keys is an essential part of any cryptographic system.
What are Public and Private Keys in Cryptography?
Public and private keys are a pair of cryptographic keys that are used to encrypt and decrypt data. The public key is freely available to anyone who wants to send a message or data securely, while the private key is kept secret and only known to the intended recipient.
What is Public Key Cryptography?
Public key cryptography is a cryptographic system that uses two keys: a public key and a private key. The public key is used for encryption, and the private key is used for decryption. In this system, anyone can use the public key to encrypt a message, but only the person who holds the private key can decrypt it. Therefore, the private key should be kept secret and protected.
The idea of public key cryptography was first introduced by Whitfield Diffie and Martin Hellman in 1976. They proposed the use of a two-key system, where one key is used for encryption, and the other key is used for decryption. The two keys are mathematically related, but it is computationally infeasible to derive the private key from the public key.
Applications of Public Key Cryptography
Public key cryptography has many applications in modern cryptography and is widely used in various fields, including:
Digital Signatures: Public key cryptography is used to create digital signatures, which are used to verify the authenticity of electronic documents.
Secure Communication: Public key cryptography is used to establish secure communication channels between two parties.
Key Exchange: Public key cryptography is used to securely exchange keys for symmetric encryption algorithms.
Secure Electronic Transactions: Public key cryptography is used to secure electronic transactions by encrypting sensitive information.
When a message or data is encrypted using the public key, it can only be decrypted using the corresponding private key. This means that even if someone intercepts the message or data, they will not be able to read it without the private key.
What is Private Key Cryptography?
Private key cryptography is a cryptographic system that uses a single secret key for both encryption and decryption of messages. The secret key is shared between the sender and the recipient and is kept secret from any other parties. The key can be any sequence of characters that is difficult to guess or crack. The strength of the encryption depends on the length and randomness of the secret key.
Private key cryptography is also known as symmetric-key cryptography because the same key is used for both encryption and decryption. The sender encrypts the message using the secret key, and the recipient decrypts the message using the same key. The security of the system relies on the secrecy of the key.
Applications of Private Key Cryptography
Private key cryptography has many applications in modern cryptography and is widely used in various fields, including:
Secure Communication: Private key cryptography is used to establish secure communication channels between two parties.
File Encryption: Private key cryptography is used to encrypt files and data stored on electronic devices.
Password Protection: Private key cryptography is used to protect passwords and other sensitive information.
Secure Email: Private key cryptography is used to secure email messages and attachments.
How do Public and Private Keys Work?
Public key cryptography uses complex mathematical algorithms to encrypt and decrypt messages. The two keys in this system are mathematically related but are designed in such a way that it is computationally infeasible to derive the private key from the public key. This property of the system makes it very secure and reliable.
Private key cryptography uses complex mathematical algorithms to encrypt and decrypt messages. The same secret key is used for both encryption and decryption. The strength of the encryption depends on the length and randomness of the secret key.
Public and private keys are based on complex mathematical algorithms that make it virtually impossible to decrypt a message or data without the corresponding private key. The most commonly used algorithm for public key cryptography is RSA (Rivest-Shamir-Adleman).
When a user wants to send a message or data to another user securely, they first obtain the recipient’s public key. They then use the public key to encrypt the message or data before sending it. Only the recipient, who has the corresponding private key, can decrypt the message or data and read it.
How Public Key Cryptography Works
Public key cryptography works by using a pair of keys – a public key and a private key – to encrypt and decrypt data. Data is encrypted using public keys, and decrypted using private keys.
When a user wants to send a message or data to another user securely, they first obtain the recipient’s public key. They then use the public key to encrypt the message or data before sending it. Only the recipient, who has the corresponding private key, can decrypt the message or data and read it.
Public key cryptography is based on the fact that certain mathematical problems are difficult to solve. The RSA algorithm, for example, is based on the difficulty of factoring large numbers into their prime factors. The security of public key cryptography relies on the fact that it would take an impractical amount of time for a computer to solve these mathematical problems, making it virtually impossible for anyone to decrypt the data without the corresponding private key.
How Private Key Cryptography Works
The same key is used for both encryption and decryption in private key cryptography, commonly referred to as symmetric cryptography. This means that the sender and receiver must both have access to the key since it is used to both encrypt and decrypt data.
In private key cryptography, the sender encrypts the message or data using the key, and the receiver uses the same key to decrypt the message or data. This method of encryption is often used for secure communication between two parties who have already established a shared secret key.
To illustrate how public key cryptography works, let’s consider the following example:
Alice wants to send a confidential message to Bob. To do this, she first needs Bob’s public key. Bob has two keys: a public key and a private key. Bob makes his public key available to anyone who wants to send him a message.
Alice uses Bob’s public key to encrypt the message. The message can only be decrypted using Bob’s private key, which is known only to Bob. Therefore, even if someone intercepts the message during transmission, they cannot read it without the private key.
Once Bob receives the encrypted message, he uses his private key to decrypt it. The message is now readable and can be understood by Bob.
In this example, the public key is used for encryption, and the private key is used for decryption. The message is secure because only Bob can decrypt it using his private key.
The Difference between Public and Private Keys
Public keys are used to encrypt data and are shared publicly, while private keys are used to decrypt the data and are kept private.
Here are 10 key differences between Private Key and Public Key in cryptography, presented in a table format:
| Feature | Private Key | Public Key |
| Purpose | Used for decryption and digital signing | Used for encryption and digital verification |
| Distribution | Known only to the owner | Can be shared with anyone |
| Size | Smaller (usually 2048-bit) | Larger (usually 4096-bit) |
| Speed of operation | Faster | Slower |
| Security | More secure due to limited distribution | Less secure due to widespread distribution |
| Key management | Requires secure storage and backup | Easier to manage and distribute |
| Complexity | More complex, involving advanced algorithms | Less complex, involving simpler algorithms |
| Usage | Used in symmetric encryption and digital signing | Used in asymmetric encryption and verification |
| Authentication | Provides strong authentication and identification | Limited authentication capabilities |
| Vulnerability to attacks | Susceptible to attacks such as brute force | Susceptible to attacks such as man-in-the-middle |
Is it possible to derive private keys from public key?
No, it is not possible to derive a private key from a public key in most commonly used public key cryptography algorithms, such as RSA or Elliptic Curve Cryptography (ECC).
The public key is generated from the private key using a mathematical function, and the function is designed to be one-way, meaning it cannot be easily reversed to derive the private key from the public key. This is important for the security of the system, as the private key must be kept secret to ensure that only the owner can decrypt messages or sign transactions.
However, it is possible to crack some weaker encryption schemes or if there is an implementation vulnerability, but with the secure implementation of widely used algorithms, it is not possible to do so. It is always essential to use secure and widely accepted encryption algorithms and practices to avoid any security breaches.
The Importance of Public and Private Keys in Cybersecurity
Public and private keys are a crucial part of cybersecurity because they provide a secure method for encrypting and decrypting data. This method ensures that sensitive information can only be accessed by authorized parties, and that it cannot be intercepted and read by anyone who gains access to it.
Public and private keys are used in a wide range of applications, including:
Secure communication: Public and private keys are used to encrypt emails, instant messages, and other forms of digital communication.
Secure file transfer: Public and private keys are used to encrypt files before they are transferred over the internet.
Digital signatures: Public and private keys are used to create and verify digital signatures, ensuring that documents and transactions are authentic and have not been tampered with.
Online transactions: Public and private keys are used to secure online transactions, such as those made with credit cards or other payment methods.
Best Practices for Using Public and Private Keys
To ensure the security of your public and private keys, it is important to follow best practices when using them. These best practices include:
Keep your private key secure: Your private key should be kept in a secure location, such as a password-protected file or a hardware device.
Use strong passwords: When creating passwords for your private key, use strong passwords that are difficult to guess.
Use two-factor authentication: Consider using two-factor authentication to add an extra layer of security to your public and private keys.
Rotate your keys regularly: Consider rotating your public and private keys regularly to ensure that they remain secure over time.
Don’t share your private key: Your private key should be kept confidential and never shared with anyone else.
Use reputable software: When generating, using, or managing your public and private keys, use reputable software that is known to be secure and reliable.
Monitor your keys: Regularly monitor your public and private keys to ensure that they have not been compromised or accessed without authorization.
Frequently Asked Questions (FAQs)
Q: Can public and private keys be used for authentication?
A: Yes, public and private keys can be used for authentication, such as in the case of SSH logins or digital signatures.
Q: Can public and private keys be reused?
A: Public keys can be reused, but private keys should not be reused.
Q: How long do public and private keys last?
A: The lifespan of public and private keys depends on the algorithm used and the level of security required. Keys may need to be rotated periodically to maintain security.
- Fiat Currency vs Bitcoin: Understanding the Differences (March 6, 2023)
- CBDC vs Bitcoin: Key Differences 2023 (March 6, 2023)
- What is a Blockchain Smart Contract? (March 5, 2023)
- Bitcoin Lightning Network and how does it work? (March 4, 2023)
- Monthly Crypto News February 2023 (March 3, 2023)
- Reasons to add Bitcoin to your portfolio (March 3, 2023)
- What Is a Cryptocurrency ATM And How Does It Work? (March 3, 2023)
- Can cryptocurrency go mainstream? (March 3, 2023)
- How Crypto Mining Stabilizes Power Grids (March 3, 2023)
- Debunking Common Misconceptions About Bitcoin (March 3, 2023)
- Decentralized Finance: Everything You Need to Know About the New Financial Technology (March 3, 2023)
- Crypto Debit Cards 101: A Beginner’s Guide (March 2, 2023)
- Why Silvergate’s Stock Price Crashed 46% After Coinbase Ended Payment Transactions (March 2, 2023)
- Cryptocurrency ETF: A Comprehensive Guide on How it Works (March 2, 2023)
- Crypto ETF Trading Made Easy: Tips for Beginners (March 2, 2023)
- What Happened To FTX? The Biggest Crypto SCAM Explained (March 2, 2023)
- Best crypto exchange in United Kingdom 2023 (March 2, 2023)
- Crypto Exchanges vs Crypto Wallets (March 2, 2023)
- What does it mean to wrap Bitcoin (March 1, 2023)
- Best crypto learning resources on the internet. (February 28, 2023)
- The Impact of Lost Bitcoin on Your Portfolio (February 28, 2023)
- Can I buy NFTs with Bitcoin? (February 28, 2023)
- What You Need to Know About Bitcoin ETFs Before Investing (February 27, 2023)
- Best crypto stock in 2023 (February 26, 2023)
- Crypto index fund (February 26, 2023)
- Fiat vs. Crypto: What’s The Difference? (February 24, 2023)
- Dollar Cost Averaging: The Best Way to Buy Bitcoin (February 23, 2023)
- The 10 most popular stablecoins in crypto (February 23, 2023)
- What Is Cryptocurrency mining? (February 20, 2023)
- Can I use a cryptocurrency exchange to avoid paying taxes? (February 20, 2023)
- What happens if the exchange I am using goes bankrupt or out of business? (February 20, 2023)
- How do I keep my cryptocurrencies and my exchange account secure? (February 20, 2023)
- What is an ICO, and can I participate in one on a cryptocurrency exchange? (February 20, 2023)
- Can I use a cryptocurrency exchange to store my cryptocurrencies for the long-term? (February 20, 2023)
- How do I know if a cryptocurrency exchange is trustworthy and legitimate? (February 20, 2023)
- What is a cryptocurrency trading bot? (February 20, 2023)
- Can I trade cryptocurrencies anonymously on an exchange? (February 20, 2023)
- Can I use a credit or debit card to purchase cryptocurrencies on an exchange? (February 19, 2023)
- Is my personal information and funds secure on a cryptocurrency exchange? (February 19, 2023)
- Can I use a cryptocurrency exchange if I’m not located in a specific country? (February 19, 2023)
- Are there any fees for using a cryptocurrency exchange? (February 19, 2023)
- Best Crypto Exchange China 2023 (February 19, 2023)
- What is the process of buying and selling cryptocurrencies on an exchange? (February 19, 2023)
- What is margin trading on a cryptocurrency exchange? (February 19, 2023)
- What is a stop-loss order on a cryptocurrency exchange? (February 19, 2023)
- What is a limit order on a cryptocurrency exchange? (February 19, 2023)
- Best Crypto Exchange Taiwan 2023 (February 19, 2023)
- What is a market order on a cryptocurrency exchange? (February 19, 2023)
- What is a maker and taker fee on a cryptocurrency exchange? (February 19, 2023)
- What is a trade pair on a cryptocurrency exchange? (February 19, 2023)
Rabi is the founder of Cryptoetf.in and a regular contributor. He is passionate about the crypto world and keeps up-to-date with the latest developments, always eager to share his knowledge with readers.